本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。如若转载,请注明出处:http://www.ldbm.cn/database/54886.html
如若内容造成侵权/违法违规/事实不符,请联系编程新知网进行投诉反馈email:809451989@qq.com,一经查实,立即删除!相关文章
实用测评!7种方式将PDF导出为图片,pdf转jpg一键转换!
pdf怎么转换成jpg?pdf是一种通用的便携文件格式之一,而jpg是一种广泛使用的图像格式,平时处理这两种格式文件时,难免会遇到需要将pdf转成jpg格式的情况,例如在学术研究、创意设计、报告提交等领域。 pdf转jpg是一个很常…
渗透测试综合靶场 DC-2 通关详解
一、准备阶段 准备工具如Kali Linux,下载并设置DC-2靶场机。确保攻击机和靶机在同一网络段,通常设置为桥接模式或NAT模式。 1.1 靶机描述
Much like DC-1, DC-2 is another purposely built vulnerable lab for the purpose of gaining experience in …
边缘智能-大模型架构初探
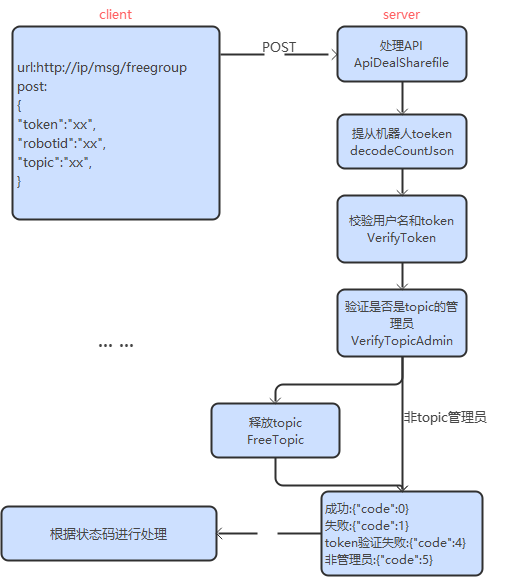
R2Cloud接口
机器人注册
请求和应答
注册是一个简单的 HTTP 接口,根据机器人/用户信息注册,创建一个新机器人。
请求 URL
URLhttp://ip/robot/regTypePOSTHTTP Version1.1Content-Typeapplication/json
请求参数
Param含义Rule是否必须缺省roboti…
结构开发笔记(八):solidworks软件(七):装配图中让摄像头绕轴旋转起来
若该文为原创文章,转载请注明原文出处 本文章博客地址:https://hpzwl.blog.csdn.net/article/details/142176639
长沙红胖子Qt(长沙创微智科)博文大全:开发技术集合(包含Qt实用技术、树莓派、三维、OpenCV…
五大注入攻击网络安全类型介绍
1. SQL注入(SQL Injection) SQL注入流程
1.1. 概述 SQL注入是最常见的注入攻击类型之一,攻击者通过在输入字段中插入恶意的SQL代码来改变原本的SQL逻辑或执行额外的SQL语句,来操控数据库执行未授权的操作(如拖库、获取…
STM32MP157/linux驱动学习记录(二)
38.Linux INPUT 子系统实验
按键、鼠标、键盘、触摸屏等都属于输入(input)设备,Linux 内核为此专门做了一个叫做 input子系统的框架来处理输入事件。输入设备本质上还是字符设备,只是在此基础上套上了 input 框架,用户只需要负责上报输入事件…
下载 llama2-7b-hf 全流程【小白踩坑记录】
1、文件转换
在官网 https://ai.meta.com/llama/ 申请一个账号,选择要下载的模型,会收到一个邮件,邮件中介绍了下载方法 执行命令 git clone https://github.com/meta-llama/llama.git ,然后执行 llama/download.sh,…
Jetbrains开发工具使用通义灵码
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档 文章目录 前言一、安装二、使用步骤1.模型选择2.存在的问题 总结 前言
之前用过tabnine等AI工具,tabnine还行,有免费版,但是效果有限&…
LED智慧一体机已成为高端超微小间距COB显示领域的风向标
LED智慧一体机成为推动智能会议、高效办公与教育创新的强大引擎。本文将深入剖析晶锐创显LED智慧一体机的技术革新、功能集成、应用场景以及其对未来显示技术发展的深远影响。
1、技术革新:COB超高清显示技术的璀璨绽放
LED智慧一体机之所以能在众多显示产品中脱…
基于python+django+vue的医院预约挂号系统
作者:计算机学姐 开发技术:SpringBoot、SSM、Vue、MySQL、JSP、ElementUI、Python、小程序等,“文末源码”。 专栏推荐:前后端分离项目源码、SpringBoot项目源码、SSM项目源码 系统展示
【2025最新】基于协同过滤pythondjangovue…
python毕业设计基于django+vue医院社区医疗挂号预约综合管理系统7918h-pycharm-flask
目录 技术栈和环境说明预期达到的目标具体实现截图系统设计Python技术介绍django框架介绍flask框架介绍解决的思路性能/安全/负载方面可行性分析论证python-flask核心代码部分展示python-django核心代码部分展示操作可行性技术路线感恩大学老师和同学详细视频演示源码获取 技术…
Linux权限管理: 文件访问者分类、文件类型和访问权限、权限值的表示方法、文件访问权限的相关设置方法、umask、目录的权限、粘滞位等的介绍
文章目录 前言一、文件访问者分类二、文件类型和访问权限1. 文件类型2. 基本权限 三、权限值的表示方法1. 字符表示方法2. 8进制数值表示方法 四、文件访问权限的相关设置方法1. chmod2. chown3. chgrp 五、 umask六、目录的权限七、粘滞位总结 前言
Linux权限管理:…
【JavaEE初阶】多线程6(线程池\定时器)
欢迎关注个人主页:逸狼 创造不易,可以点点赞吗~ 如有错误,欢迎指出~ 目录 实例3:线程池 参数解释 核心线程数, 最大线程数 允许空闲的最大时间 ,时间单位 任务队列(阻塞队列) 线程工厂>工厂设计模式 拒绝策略 使用举例 模拟实现一个线…
MySQL高阶1783-大满贯数量
题目
找出每一个球员赢得大满贯比赛的次数。结果不包含没有赢得比赛的球员的ID 。
结果集 无顺序要求 。
准备数据
Create table If Not Exists Players (player_id int, player_name varchar(20));
Create table If Not Exists Championships (year int, Wimbledon int, F…
无人机培训机构技术股份合作探讨
随着无人机技术的飞速发展,其在航拍、农业、物流、环境监测、应急救援等多个领域展现出巨大潜力,市场对无人机专业人才的需求急剧增加。鉴于此,多家致力于无人机培训教育的机构决定携手合作,通过技术股份合作模式,共同…
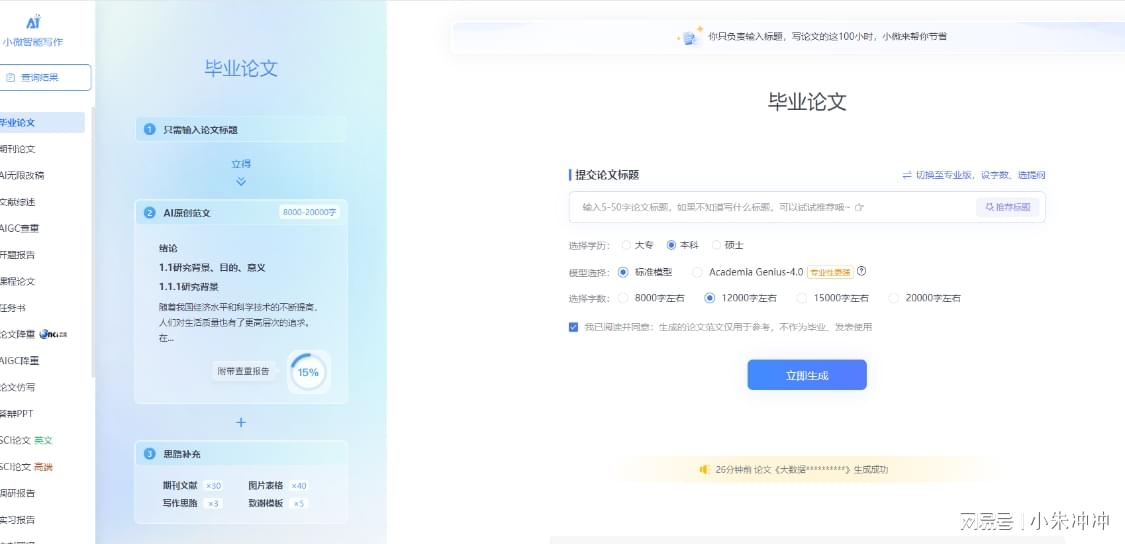
论文不会写?分享6款AI论文写作免费一键生成网站!
在当今学术研究和写作领域,AI论文写作工具的出现极大地提高了写作效率和质量。这些工具不仅能够帮助研究人员快速生成论文草稿,还能进行内容优化、查重和排版等操作。本文将分享6款免费一键生成AI论文写作网站,并重点推荐千笔-AIPassPaper。 …
力扣123-买卖股票的最佳时机 III(Java详细题解)
题目链接:123. 买卖股票的最佳时机 III - 力扣(LeetCode)
前情提要:
本题是由122. 买卖股票的最佳时机 II - 力扣(LeetCode)变形而来,122是只能买卖多次股票,该题是只能买卖俩次股…